Safeguarding your company’s assets is a formidable challenge when everything is easily accessible. If you work with pricey equipment, confidential information, and a vast industry, security must be the priority for your organization. Whether you have a team of 10 people or 10000 employees, a highly dignified access control system can facilitate their needs and outnumber those not on the list.
However, with advancements in technology, access control, and cloud computing can become a necessary double-edged sword. It’s no doubt that the access control system has made business processes efficient and hassle-free; it can also put sensitive data at risk if you don’t have high security and knowledge about managing the system.
Whether you are an administrator or a business owner, the security of the company, employees, and sensitive data is your first-hand priority. In this guide, you will get all the answers to your queries regarding the access control system and its role in the coming few generations.
Read More: Why choose the right IoT platform development for your business?
What are the Components of Access Control?
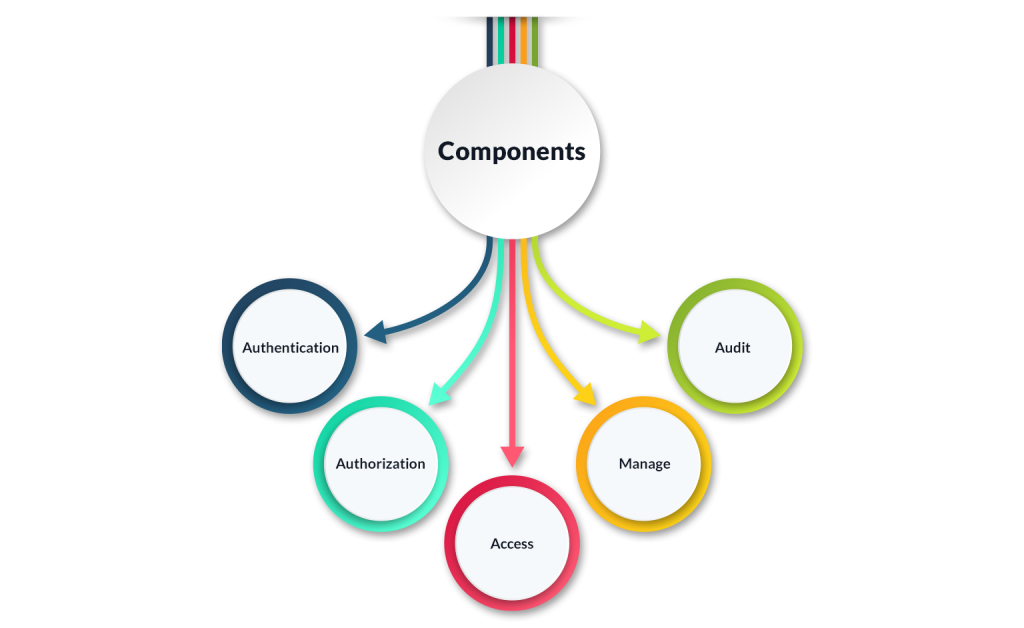
Organizations want a mechanism to monitor and manage access in addition to being able to regulate who enters through their doors. Computer-based gadgets and systems have taken the place of keys in granting rapid, convenient access to authorized people while restricting access to unauthorized ones.
Authentication: This is the act of demonstrating the user’s identification. This could entail confirming the legitimacy of a website’s digital certificate, approving a form of identification, or contrasting login credentials with stored information.
Authorization: This details a staff member’s access to particular resources.
Access: Only a person can access the resource after being authenticated and granted access.
Manage: The authorization and authentication of systems or users can be added or removed by the system. In addition, some applications simplify maintenance by synchronizing with Azure Active Directory or G Suite.
Audit: The “least privilege” principle is enforced by this; in essence, audits reduce the possibility of users having access to resources they no longer require.
Read More: Guide for selecting Antennas for your next IoT device
How does Access Control Works?
A business may employ an intercom or an electronic system that uses access card readers, user credentials, audits, and reporting. Or, it might compare a person’s identification with its integrated set of access regulations using biometrics as identity authentication.
Another option is multi-factor authentication (MFA), which requires a user to be something (biometrics) and know something (a password) to proceed (a 2FA SMS authentication code).
Access control systems typically function by identifying a person, confirming that they are who they claim to be, approving their access to the place or resource, and correlating their actions with their username or IP address for auditing reasons.
Types of Access Systems
External security devices must communicate with access control systems, and there are standard ways to do this. For example, systems based on a smartphone, the cloud, or the Internet of Things (IoT) can help establish a connection between the server and the reader.
Cloud-based Access Control
These systems use cloud-based software to store logs, data, credentials, and other information on a distant server. The fundamental benefit of cloud-based communication is that you may access your account from anywhere as long as you have a secure Internet connection. Companies may now effortlessly coordinate systems from multiple offices as well.
IoT-based Access Control

The reader and control panel are connected using a dedicated server in these systems. Access is available to users using internet-based protocols.
Smartphone-based Control

The system allows users to log in using a smartphone app. The software allows an administrator to examine saved data, remotely access the system, and make changes. In addition, the software allows users to access restricted areas and verifies their authorization at the reader’s site. Simply sign in to the app, place your mobile next to the scanner, and you will instantly be granted access to the restricted area.
Why is Access Control Important?
By tracking when people enter and leave specific rooms and areas, access control is a system that can help you better understand the utilization of a building or site. It can also increase the overall security of your site.
In an emergency, such as a fire, it is crucial to know who is in your facility during that time. Additionally, an access control system prevents unauthorized individuals from entering your property, which may be crucial in settings like schools and care facilities.
Exist hazardous equipment or private information on the premises? Some areas might not be accessible to all of your staff. Therefore, access control can aid in keeping you and your staff members safe.
Conclusion
Access controls are a crucial component of a framework for information security. After reading this manual, your organization will have a solid basis for managing user access to data and systems that satisfy all legal, contractual, statutory, and regulatory obligations.
The constant evolution of physical and virtual risks necessitates using cutting-edge technology, in-depth analytics, and strict safety protocols. Simple passwords and keys are no longer sufficient. The access control system can help improve the security of your information and physical assets effectively.
Get in contact if you’d like to learn how to clearly define access control in a model or policy for your organization.