By creating customized policies, an organization can use the Access Control system in cloud security to control and monitor rights to its business data. However, given their on-demand services and mobility, cloud apps might not be able to provide the macro-level visibility into data and user activity that access control in cloud security enables.
Data breaching will indicate a problem with the industry’s access control system. These systems expose the information to publicly available systems, making the crucial components susceptible to unauthorized data retrieval. In addition, the system can be hacked and breached from anywhere around the globe. As a result, network connectivity has become a crucial asset for industries.
However, Axess.ai in cloud security lets companies formulate policies to restrict access through specific IP addresses, browsers, devices, and during specified time shifts.
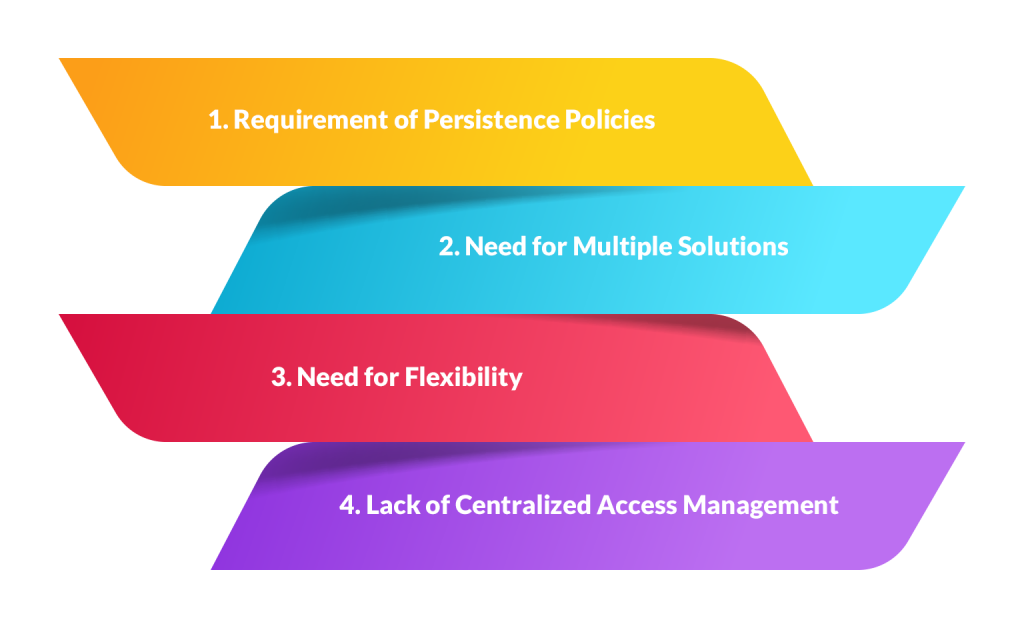
Requirement of Persistence Policies
The proper access control system must be chosen based on the type and model of data processing used in the plant. Role-based control may be permitted depending on the complexity of the company’s organizational structure.
The more knowledgeable person can implement the attribute-based high-security access control. Depending on the system being used, the security of the connection, the geolocation, and the time of activity on the data, this may involve access.
A sophisticated system will ensure the data is secure by enabling dynamic changes to the access controls. The access control regulations must be modified depending on the risk variables present.
Deploying security analytics layers employing AI and machine learning is essential to convey this. For example, real-time dangers can be mapped using the patterns identified by machine learning technology, and the controls can be adjusted accordingly.
Need for Multiple Solutions
Security in the IoT is more complicated than in previous, more monolithic computing settings because of the dispersed nature of the technology, which allows vast numbers of autonomously communicating devices to communicate across numerous standards and protocols.
The IoT sector will also need to adapt traditional access control and authentication models and protocols to this new paradigm. For example, companies can identify IoT devices, isolate compromised nodes, verify data integrity, authenticate users, and authorize various degrees of data access with the help of the appropriate access control and authentication frameworks.
Need for Flexibility
Many businesses frequently become exposed to cloud misconfigurations, which are once again a source of vulnerability due to the speed with which cloud operations are conducted and the ambiguity that results from who is in charge of what security-related factors.
Due to the numerous configurations and potential problems around it, such as password policy, incorrect user authentication, gaps in logging and reporting, and other issues, IAM is a significant source of risk for many businesses.
Lack of Centralized Access Management
When it comes to access control, one of the most frequent errors is password management. It’s not unusual for employees and even business owners to use the same password everywhere when many distinct systems need a password to access them.
However, even when employees are compelled to change their passwords frequently, the issue of employing passwords that are weak and simple to guess persists. In addition, many individuals are guilty of using the same password on different systems. It makes sense that individuals would do this, given how difficult it may be to remember different passwords.
The promotion of password-keeper apps is an excellent answer to this issue. As a result, you and your staff can use different, secure passwords for every system without memorizing them. But, first, you must ensure that your “keeper app” is secure before you unlock every system door.
Lock your Access Control with Axess.ai

The market is heating up, and to stay ahead of the escalating competition in every sector, real-time analytics and strategy are required. When information is exposed in this way, it is simple for rival services to outperform one another in terms of the level of personalization.
Secure access control systems thereby provide security for sensitive data and data centers. In addition, enterprises will be able to scale up their security standards and utilize protected data thanks to the compact architecture of this technology’s essential components, such as policy enforcement, endpoint agents, and enforcement points. Axess.ai’s axess engine is built to scale and integrate with your existing security devices without being locked into any hardware ecosystem. Using security features and protocols is unparalleled in the access control industry.