Overview
The Physical Access Control Market is an ever-growing sector enjoying ever-growing demand and prevalence, with nearly 45% of employees having determined access control systems to be pivotal for a smart lock and digital security within their offices.
Its usage has been employed and has seen steady growth in various market sectors, such as private organizations and public spaces, especially within government agencies. According to factmr.com, demand for physical access control systems increased by more than 10% in 2021, reaching 2.2 million units shipped and is expected to surpass a valuation of US$ 12.7 Bn by 2031.
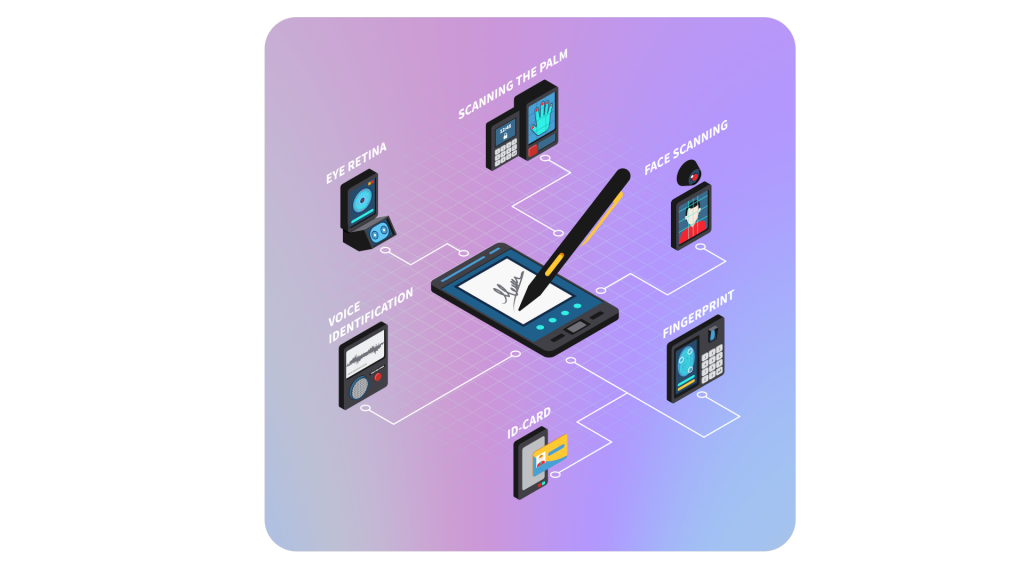
Access Control was limited to just a handful of devices connected on a single local network during its nascent years. Still, the growing demands of the market meant that if the industry players wanted to expand beyond its niche and develop Physical Access Control into a full-fledged market of its own, it needed to be connected to the internet and the cloud; else it risked being known as just a glorified version of the Lock and Key.
The need to connect everything to the cloud came from the demand to Manage and Monitor access remotely, which has resulted in the market for cloud-based access control systems, which was never really done before. There were multiple reasons and challenges on why access control systems were never really put up on the internet and were instead preferred to be deployed on local servers.
Challenges
Here are some of the reasons why internet-based physical security control systems have been a contentious topic.
- Constant internet availability and no downtimes.
- High Processing Delays
- Cyber-Security Concerns
- Federal or Local Government Policies
However, with the internet’s unprecedented growth and emerging 5G and 6G technologies, it is clear that most organizations want to shift access control to web-based platforms that can be accessed from anywhere. At the same time, the challenges mentioned earlier must be addressed.
Axess.ai has seized this opportunity to address these unique challenges by providing a web-based, secure, and dependable infrastructure that is so adaptable that such unique concerns of each organization can be managed efficiently. The following section will discuss these issues and how axess.ai plans to manage them.
Constant Internet Availability
Access Control Solutions necessitate that all requests be fulfilled without fail. You cannot make someone wait at the door simply because your server is down or the internet is down. Increasing internet availability and decreasing server downtime can make internet-based services more reliable, but we cannot tolerate even a 1% downtime in the system.

To combat this issue effectively, axess.ai provides a design to use the gateway protocol to specify whether you want to send your access control requests to a cloud server or your local gateway server. Axess.ai is also in charge of data synchronization between the two.
High Processing Delays
When expecting any result from the cloud, cloud-based systems must adhere to two major timing requirements: processing time and propagation time. While the former is associated with server infrastructure, the latter is associated with internet speed and bandwidth. Minimizing both delays comes at a cost, and most of the time, this cost is recurring. Access Control Organisations try their best to optimize and reduce these overhead costs without compromising Delay Time.
Axess.ai comes to the rescue in these types of situations by offering these organizations the following alternatives:
- One recourse would be to deploy different functionalities on different servers, such as a local gateway or some other low-cost server.
- Another possibility would be implementing the solution on the gateway itself for frequent, time-consuming requests.
Cyber-Security Concerns
Cyber-Security is a significant concern in the present day and age, and Physical Access Control Systems represent the pinnacle of this issue. Suppose any unauthorized or malicious user gains access to your Access Control System. In that case, they can cause any number of disasters. Organizations need to realize that even if they’re spending millions on building security measures within their products, it still doesn’t mean that they have Guaranteed Protection. It just takes a single vulnerability within the chain for everything else to crumble down. In this case, a publicly accessible, cloud-based access control system becomes the weakest link in the chain.

In axess.ai, we’ve considered both these scenarios; One where the organization is willing to spend money on overhead security measures and the other where the organization simply stays within its own local network and remains cut-off from the rest of the internet. For this, we’ve offered multiple types of deployments, in order to fit your use case and comfort.
Federal or Local Government Policies
Laws & Policies in countries like the United States are highly explicit on how data should be stored, where it should be held, and how it should be recovered or destroyed. Unfortunately, having a universal cloud-based system architecture makes it a challenge to meet and comply with all these requirements without affecting the product functionality.
In axess.ai, we’ve designed such flexibility to choose where your data should be stored, where it should be delivered for processing, how long it should be stored, and so on.
Conclusion
From private organizations to public spaces; the Physical Access Control Industry has taken several huge strides from its initial nascent stages. From being in the shadow of the Lock and Key Industry to now evolving into Cloud-Based Access Control System, It has built a whole market segment of its own.
However, many challenges are still upon the visionaries looking to bring this idea into reality. Axess.ai intends to be one of those visionaries looking to bring forth this dystopian future into reality.